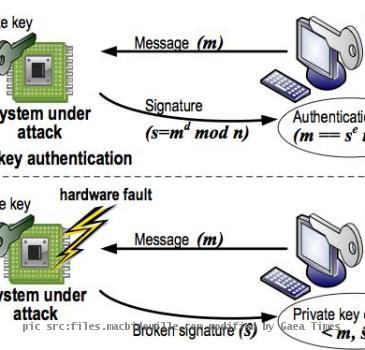
RSA Encryption method is used for almost every secured transactions and the RSA 1024 bit encryption is used in almost every banking sites and credit card transaction points. Some scientists from the University of Michigan have found that the code can be cracked in 100 hours which would otherwise take years in Brute force attacks.
The procedure makes the processor stressed with voltage regulations to the processor while it is using the keys to decode. The scientists tweaked the device’s power supply and the fluctuating voltages of the CPU generated single hardware error per clock cycle. This can cause the server to flip single bits of the private key at a time. The single pieces of the private key can now be gathered together to form the full password. They successfully hacked 1024 bits encryption using 104 hours of processing time from a small cluster of 81 Pentium 4 chips.
Now, the question arises, is this a real flaw in the RSA algorithm and do we need to worry seriously while making transactions in the websites? The direct answer would be, no. This fault is not a real fault of the RSA algorithm and we don’t need to worry about it because, to crack a password in this method one would need to plant a voltage tampering system within your system and it can’t be done remotely. This is a type of side channel attack that requires a physical access to the hardware involved with the cryptosystems. This means, unless a thief literally breaks into your house and plants a device within your computer, there is no need to worry!