Pure Salon & Spa Koramangla, Bangalore
Pure Salon & Spa Koramangla, Bangalore
Led by veteran hair stylist Pure Salon & Spa offers various services from the simple hair cut and styling for women, men, kids, and brides, to vibrant hair colours, conditioning treatments, and Brazilian blowouts. Located at the heart of Koramangla, Bangalore, the salon has been around since 2015, providing professional hair treatments in a relaxed ambience. This is definitely one of our favourite hair salons in Bangalore.
Are Xiaomi Devices Sending User Data to China? The Company Clarifies
There are several reports mentioning that Chinese company, Xiaomi’s
devices are sending user data to China. As per the reports, Xiaomi RedMi was found to be secretly sending photos and texts to China servers.

MIUI requests public data from Xiaomi servers from time to time. These include data such as preset greeting messages (thousands of jokes, holiday greetings and poems) in the Messaging app and MIUI OTA update notifications, i.e. all non-personal data that does not infringe on user privacy.
Does Xiaomi upload any personal data without my knowledge?
Answer: No. Xiaomi offers a service called Mi Cloud that enables users to back up and manage personal information in the cloud, as well as sync to other devices. This includes contacts, notes, text messages and photos. Mi Cloud is turned off by default. Users must log in with their Mi accounts and manually turn on Mi Cloud. They also have the option to only turn on backup for certain types of data. The use and storage of data in Mi Cloud fully respects the local laws of each country and region. Strict encryption algorithms are implemented to protect user privacy.
And Importantly, Why should one believe Xiaomi?
Answer: Xiaomi is serious about user privacy and takes all possible steps to ensure our Internet services adhere to our privacy policy. We do not upload any personal information and data without the permission of users. In a globalized economy, Chinese manufacturers’ handsets are selling well internationally, and many international brands are similarly successful in China – any unlawful activity would be greatly detrimental to a company’s global expansion efforts.
–
Ofcourse, you can switch off MiUI Cloud off in settings.

Xiaomi Sending Data To China? [Image credit:http://en.ocworkbench.com/]
So what is being sent to the servers? What surprises the tester is that even if you root the phone and flash it with another firmware, the background transmission continues. It seems that the process is hard coded into the phone.[Via]Xiaomi (India) has clarified this privacy issue on its Facebook page.
MIUI requests public data from Xiaomi servers from time to time. These include data such as preset greeting messages (thousands of jokes, holiday greetings and poems) in the Messaging app and MIUI OTA update notifications, i.e. all non-personal data that does not infringe on user privacy.
Does Xiaomi upload any personal data without my knowledge?
Answer: No. Xiaomi offers a service called Mi Cloud that enables users to back up and manage personal information in the cloud, as well as sync to other devices. This includes contacts, notes, text messages and photos. Mi Cloud is turned off by default. Users must log in with their Mi accounts and manually turn on Mi Cloud. They also have the option to only turn on backup for certain types of data. The use and storage of data in Mi Cloud fully respects the local laws of each country and region. Strict encryption algorithms are implemented to protect user privacy.
And Importantly, Why should one believe Xiaomi?
Answer: Xiaomi is serious about user privacy and takes all possible steps to ensure our Internet services adhere to our privacy policy. We do not upload any personal information and data without the permission of users. In a globalized economy, Chinese manufacturers’ handsets are selling well internationally, and many international brands are similarly successful in China – any unlawful activity would be greatly detrimental to a company’s global expansion efforts.
–
Ofcourse, you can switch off MiUI Cloud off in settings.
Codenamed hackers from secret Chinese military unit Unit 61398 charged in world-first move by US

Charged, but not in custody ... the alleged Chinese spies. The Obama Administration said it ‘will not tolerate’ hacking.
Source: AFP
THE US has charged five members of a shadowy Chinese military unit
for allegedly hacking US companies for trade secrets, infuriating
Beijing which suspended cooperation on cyber issues.
Hacking has long been a major sticking point in relations between
the world’s two largest economies, but Washington’s move marks a major
escalation in the dispute.

UglyGorilla is alleged to belong to a
crack force of Chinese cyber-spies known as Unit 61398, believed to be
part of the country’s People’s Liberation Army. Picture: AP
Source: AP

Last year, a report suggested this
non-descript 12-storey building on the outskirts of Shanghai houses Unit
61398 of China’s PLA. Picture: AP
Source: NewsComAu
Attorney General Eric Holder called on China to hand over the five men for trial in the steel city of Pittsburgh and said the United States would use “all the means that are available to us” should Beijing refuse.

Each of the cyber-spies was codenamed. Picture: AP
Source: AP

hzy—lhx is wanted by the FBI. Picture: AP
Source: AP
“This case should serve as a wake-up call to the seriousness of the ongoing cyber threat,” Holder told reporters.
The grand jury indicted each of the five — Wang Dong, Sun Kailiang, Wen Xinyu, Huang Zhenyu and Gu Chunhui — on 31 counts, which each carry penalties of up to 15 years in prison.

‘Any means available’ ... Attorney General Eric Holder has warned China over the hackers.
Source: AP
A report last year by security firm Mandiant said that the unit had thousands of workers operating out of a nondescript, 12-story building on the outskirts of Shanghai where they pilfer intellectual property and government secrets.
China swiftly responded, calling the US indictment “ungrounded and absurd” and saying it “grossly violates the basic norms governing international relations and jeopardises China-US cooperation and mutual trust.”
Anatomy of a hack: How crackers ransack passwords like “qeadzcwrsfxv1331”
For Ars, three crackers have at 16,000+ hashed passcodes—with 90 percent success.

Thanks to the XKCD comic, every password cracking word list in the world probably has correcthorsebatterystaple in it already.
Aurich Lawson
Imagine no more. We asked three cracking experts to attack the same list Anderson targeted and recount the results in all their color and technical detail Iron Chef style. The results, to say the least, were eye opening because they show how quickly even long passwords with letters, numbers, and symbols can be discovered.
The list contained 16,449 passwords converted into hashes using the MD5 cryptographic hash function. Security-conscious websites never store passwords in plaintext. Instead, they work only with these so-called one-way hashes, which are incapable of being mathematically converted back into the letters, numbers, and symbols originally chosen by the user. In the event of a security breach that exposes the password data, an attacker still must painstakingly guess the plaintext for each hash—for instance, they must guess that "5f4dcc3b5aa765d61d8327deb882cf99" and "7c6a180b36896a0a8c02787eeafb0e4c" are the MD5 hashes for "password" and "password1" respectively. (For more details on password hashing, see the earlier Ars feature "Why passwords have never been weaker—and crackers have never been stronger.")
While Anderson's 47-percent success rate is impressive, it's miniscule when compared to what real crackers can do, as Anderson himself made clear. To prove the point, we gave them the same list and watched over their shoulders as they tore it to shreds. To put it mildly, they didn't disappoint. Even the least successful cracker of our trio—who used the least amount of hardware, devoted only one hour, used a tiny word list, and conducted an interview throughout the process—was able to decipher 62 percent of the passwords. Our top cracker snagged 90 percent of them.
The Ars password team included a developer of cracking software, a security consultant, and an anonymous cracker. The most thorough of the three cracks was carried out by Jeremi Gosney, a password expert with Stricture Consulting Group. Using a commodity computer with a single AMD Radeon 7970 graphics card, it took him 20 hours to crack 14,734 of the hashes, a 90-percent success rate. Jens Steube, the lead developer behind oclHashcat-plus, achieved impressive results as well. (oclHashcat-plus is the freely available password-cracking software both Anderson and all crackers in this article used.) Steube unscrambled 13,486 hashes (82 percent) in a little more than one hour, using a slightly more powerful machine that contained two AMD Radeon 6990 graphics cards. A third cracker who goes by the moniker radix deciphered 62 percent of the hashes using a computer with a single 7970 card—also in about one hour. And he probably would have cracked more had he not been peppered with questions throughout the exercise.
The list of "plains," as many crackers refer to deciphered hashes, contains the usual list of commonly used passcodes that are found in virtually every breach involving consumer websites. "123456," "1234567," and "password" are there, as is "letmein," "Destiny21," and "pizzapizza." Passwords of this ilk are hopelessly weak. Despite the additional tweaking, "p@$$word," "123456789j," "letmein1!," and "LETMEin3" are equally awful. But sprinkled among the overused and easily cracked passcodes in the leaked list are some that many readers might assume are relatively secure. ":LOL1313le" is in there, as are "Coneyisland9/," "momof3g8kids," "1368555av," "n3xtb1gth1ng," "qeadzcwrsfxv1331," "m27bufford," "J21.redskin," "Garrett1993*," and "Oscar+emmy2."
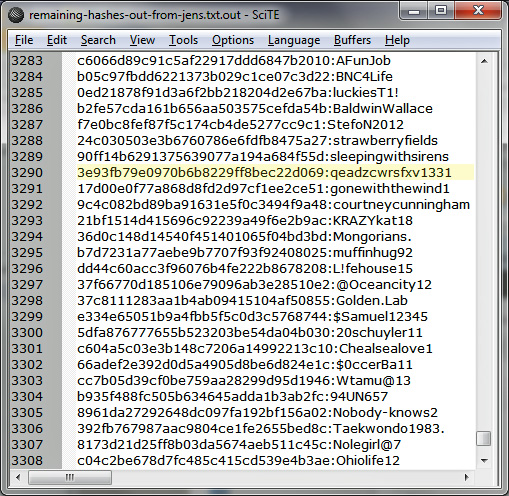
A screenshot showing a small sampling of cracked passwords.
Life in the fast lane
"These are terrible passwords," radix, who declined to give his real name, told Ars just a few minutes into run one of his hour-long cracking session. "There's probably not a complexity requirement for them. The hashing alone being MD5 tells me that they really don't care about their passwords too much, so it's probably some pre-generated site."Like SHA1, SHA3, and most other algorithms, MD5 was designed to convert plaintext into hashes, also known as "message digests," quickly and with a minimal amount of computation. That works in the favor of crackers. Armed with a single graphics processor, they can cycle through more than eight billion password combinations each second when attacking "fast" hashes. By contrast, algorithms specifically designed to protect passwords require significantly more time and computation. For instance, the SHA512crypt function included by default in Mac OS X and most Unix-based operating systems passes text through 5,000 hashing iterations. This hurdle would limit the same one-GPU cracking system to slightly less than 2,000 guesses per second. Examples of other similarly "slow" hashing algorithms include bcrypt, scrypt, and PBKDF2.
The other variable was the account holders' decision to use memorable words. The characteristics that made "momof3g8kids" and "Oscar+emmy2" easy to remember are precisely the things that allowed them to be cracked. Their basic components—"mom," "kids," "oscar," "emmy," and numbers—are a core part of even basic password-cracking lists. The increasing power of hardware and specialized software makes it trivial for crackers to combine these ingredients in literally billions of slightly different permutations. Unless the user takes great care, passwords that are easy to remember are sitting ducks in the hands of crackers.
What's more, like the other two crackers profiled in this article, radix didn't know where the password list was taken from, eliminating one of the key techniques crackers use when deciphering leaked hashes. "If I knew the site, I would go there and find out what the requirements are," he said. The information would have allowed radix to craft custom rule sets targeted at the specific hashes he was trying to crack.
How to Hack Google Like NSA's Top Cyberspies

Thanks to a FOIA request filed in April by MuckRock, a service that files FOIA requests on behalf of journalists and others, you can learn to surf the web like one of the NSA’s top cyber sleuths. The agency recently released a 643-page book, called Untangling the Web: A Guide to Internet Research, that is full of tips on doing web research — including an entire section dedicated to “Google Hacking.”
What is Google hacking? The author of NSA’s book is quick to note that there is nothing unknown or illegal about the practice — noting that much of it was first revealed in Johnny Long’s 2004 book “Google Hacking for Penetration Testers” — but that it will help you “access publicly available information that almost certainly was not intended for public distribution” (cybersecurity professionals, take note).
Here are five of the hacking tips the author recommends.
1. Limit search by site
“This can be as broad as a country [site:fr] or as specific as an individual server on a company website [site:office.microsoft.com].”2. Be as specific as possible
“You will have a lot more success searching for information within the Chinese Ministry of Foreign Affairs [site:fmprce.cn.gov] than looking at all the sites indexed for China [site:cn] or even for the government of China [site:gov.cn].”3. Add keywords
“Here’s where your subject matter knowledge and creativity really help. You are the best source of information about what words are most likely to yield the best quality and quantity of useful information. As a general rule, more uncommon words work best (consider using unusual proper names).”4. Limit search by file type
“Most of the best information found by Google hackers is not on webpages (HTML) but in other types of files. Try all or most of the file types one at a time (these are not the only searchable types; check the particular search engine’s documentation . . . for others.”5. Use Google hacking techniques to search inside websites requiring registration
“You will frequently encounter a website, perhaps a database, that requires registration to view its contents. On occasion you can use Google to get at that data without registering.”The author of the document is quick to note that nobody should use these techniques for cracking — i.e. breaking into websites and servers — but rather, the author encourages readers to “hack” their own websites “to see what kinds of information is being revealed inadvertently via Google and other search engines.”
So, perhaps, it’s best to view it as a cyber defense manual — unless, of course, that’s not how you intend to use it.
Image via PAUL J.RICHARDS/AFP/Getty Images
Hong Kong Facebook user arrested over hacking threat
 Hong Kong police said on Sunday
they had arrested a 21-year-old man after he reportedly said on social
networking site Facebook that he would hack several government websites.
Hong Kong police said on Sunday
they had arrested a 21-year-old man after he reportedly said on social
networking site Facebook that he would hack several government websites.Police said the man, who was later released on bail, was held on suspicion of "access to a computer with criminal ordishonest intent" after he allegedly threatened to hack seven government websites between June and August this year.
"The Internet is not a virtual world of lawlessness," a police spokesman said, adding that the man was required to report back to the police in October.
The unidentified man was arrested on Friday before being released on bail, the spokesman told .He faces up to five years imprisonment if found guilty.
The man is a member of the global hacker group Anonymous,the South China Morning Post said. The group is said to have 20 members in the semi-autonomous Chinese territory, which guarantees civil liberties not seen on the mainland, including freedom of speech.
The police spokesman declined to confirm his link to Anonymous. The last posting on the "Anonymous HK" Facebook page on July 22 urged authorities to show "respect" to citizens.
The notorious group, which is believed to be a looselyaffiliated network of "hacktivists", has attacked sites of groups as varied as MasterCard and Visa, the US Justice Department, and the Tunisian and Yemen governments.
Reuters suffers double hack
Blog platform, Twitter account hijacked
By Richard Chirgwin
Call it a “psy-ops” attack, if you like: Reuters has suffered
the embarrassment of having two platforms infiltrated and used to spread
propaganda messages supporting the Syrian regime.The newswire’s woes began on Friday, August 3, when attackers gained access to its blogging platform and posted false stories claiming attributed to Reuters journalists. This included a post claiming to be an interview with Free Syrian Army (FSA) head Riad al-Assad foreshadowing a pull-out from northern Aleppo.
The Twitter hijacker’s parting shot drew in Zionist propaganda, stating that Reuters was planning a shareholders’ meeting to investigate “Rothschild’s ‘iron grip’ over decision-making process”.
As Christian Science Monitor notes, such “ham-handed” propaganda probably doesn’t have much impact (Indeed, in El Reg’s experience, it’s easier and more effective to punk newswires with urban myths, but that’s another story
Subscribe to:
Posts (Atom)